Why End-to-End Encryption Isn’t Enough


End-to-end encryption (E2EE) is widely considered the gold standard for privacy in digital communications. Many privacy-conscious users rely on messengers like Signal, Telegram, and WhatsApp, trusting their E2EE claims to protect their conversations. However, the reality is that E2EE alone does not guarantee full privacy. Critical vulnerabilities still exist, and the bigger question is: Can you truly trust that there are no backdoors?
Even if your messages are encrypted, many privacy risks remain if the messengers you use are centralized. They operate on company-controlled central servers, which can be exploited, monitored, or manipulated. Here’s why E2EE isn’t enough:
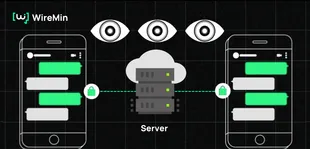
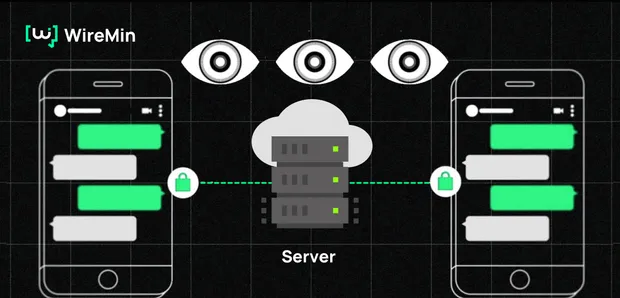
Encryption only protects the content of your messages, not the metadata surrounding them — who you talk to, when, how often, and even where. This metadata creates a comprehensive digital footprint, becoming a goldmine for governments and corporations that analyze behavioral patterns. Plus, apps like Signal require phone numbers, linking real identities to communications.
“Signal does store some metadata, including the date and time a user registered and the last date of connection.”- Forbes (2021)
When a messaging app is controlled by a single entity—as most are—it creates a centralized point of vulnerability. A single security breach can expose millions of users’ data, making it an attractive target for hackers. Meanwhile, governments can easily pressure companies to shut down services entirely.
“WhatsApp data leaked - nearly 500 million mobile phone number for sale online.”- Cybernews (2023)
“Russia's ban on Signal and other encrypted messaging apps remains in place.” -The Moscow Times (2023)
Centralized messaging apps are dangerously vulnerable to government demands and forced to introduce backdoors that compromise user privacy, allowing surveillance and data access without user consent. Privacy policies—the very documents meant to protect users—can also be quietly altered, weakening protections without users realizing it. What was once secure can quickly become compromised.
“The U.K. has ordered Apple to provide officials access to view encrypted material uploaded to the cloud” - Washington Post (2025)
“WhatsApp will be able to share user account information like your phone number, logs of how long and how often you use, device identifiers, IP addresses...” - WIRED (2021)
Decentralized messengers don’t rely on central servers. Data is stored locally on users' devices, ensuring that only you control what to share and with whom. Without a single point of failure, there is no risk of mass data breaches or unauthorized access by service providers.
Unlike centralized apps, messaging apps based on peer-to-peer (P2P) network structure send messages directly between peers/users, bypassing servers and eliminating metadata logging. With no timestamps, IP addresses, or contact records stored, no entity can track or reconstruct communication patterns, ensuring true privacy and anonymity.
No entity can track, censor, or block any user on decentralized apps like they can on centralized ones. Without a central authority controlling access, it is impossible to enforce content restrictions, introduce backdoors, and comply with surveillance demands, even under governmental pressure.
Unlike centralized apps that can shut down services or restrict access due to policies or even company bankruptcy, decentralized messengers remain operational as long as there are a reasonable number of active users. Messages are relayed directly through peers, making the network resilient, unstoppable, and immune to any authorities' impact.
Not all messengers claiming to be private are truly trustworthy. Here’s a simple checklist to help you verify if a messaging app is truly decentralized and protects your privacy.
- ✅ Can you sign up without a phone number or email?
- ✅ Can developers ban accounts or delete messages/content?
- ✅ Does the app work without a central server?
- ✅ Are messages end-to-end encrypted (E2EE) by default?
- ✅ No metadata collection (e.g., IP addresses, contact lists).
- ✅ Can the app be blocked or censored in certain regions?
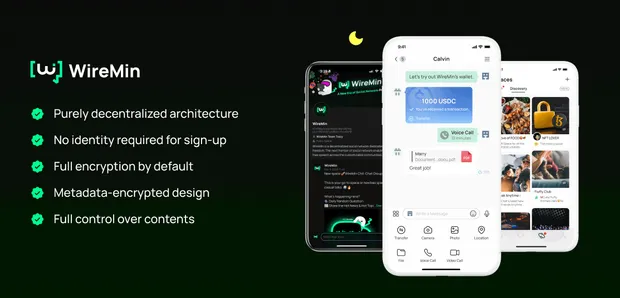
Encryption alone isn't enough; they still collect metadata and know too much about you. A decentralized messenger eliminates the need for trust, ensuring true privacy, security, and freedom from surveillance.
Decentralization isn’t just for privacy-conscious users. It also forms a hard shield for whistleblowers risking their freedom to expose corruption, journalists protecting vulnerable sources, and activists confronting powerful adversaries.
In a world where data can be a weapon, decentralized communication isn't optional—it's essential.